Man-in-the-Middle Attacks
In this part, we will discuss man-in-the-center (MITM) assaults. This is perhaps the most perilous assaults that we can do in an organization. We can perform to this assault whenever we have associated with the organization. This assault diverts the progression of parcels from any client to our gadget. This implies that any parcel that is shipped off or from the clients should go through our gadget. Presently, we know the secret word and key to the organization, so we will actually want to peruse just read those bundles, alter them, drop them. This assault is so compelling thus strong in light of the fact that it's extremely difficult to safeguard against. This is because of the manner in which the ARP convention works.
ARP has two principle security issues. The primary security issue is that every ARP demand reaction is trusted, so anything our gadget tells different gadgets that are in our organization will be relied upon. Assuming we tell any gadget on our organization that we are the switch, the gadget will trust us. It won't run any test to ensure that we are the really the switch. Similarly, assuming we let the switch know that we are another person on the organization, the switch will believe us and will begin regarding us as that gadget. So that is the primary security issue. The subsequent security issue is that clients can acknowledge reactions regardless of whether they send a solicitation. Things being what they are, the point at which a gadget associates with the organization, the principal thing it will ask is, who is the switch? And afterward the switch will send a reaction saying "I'm the switch." Now, we can simply send a reaction without the gadget asking that who the switch is. We can simply tell the gadget we are the switch, and on the grounds that the gadgets trust anybody, they will believe us and begin sending us parcels as opposed to sending the bundles to the switch.
Presently, we will figure out how this MITM assault functions. It will work utilizing a method called ARP harming, or ARP ridiculing. In the accompanying graph, we can see a common Wi-Fi organization. We will see that when the client demands someth[ing, it will send the solicitation to the Wi-Fi switch, and afterward the switch will get the solicitation from the web and return with the reactions to the Client :
Presently, this is finished utilizing bundles. Along these lines, how we will treat we will send an ARP reaction to the Client so we can send reactions without the Client asking them. The Client didn't request anything, yet we can in any case send it a reaction. We will say that our IP is the switch IP. Along these lines, the switch has the IP 192.168.0.1. We will let the Client know that the gadget with the IP 192.168.0.1 has our MAC address, so we will let the Client know that we are the switch, essentially.
Due to this, the Client will start sending the packets to us instead of sending the packets to the router. The following diagram illustrates this :
From that point onward, we will do the inverse to the Wi-Fi switch. We will let the switch know that we are the clients. We will do this by let the switch know that our IP is the Client IP, and that Client has our MAC address, so the correspondence of parcels will be done through the MAC address, and the Wi-Fi switch will begin sending bundles to us as opposed to sending it to the Client. The accompanying chart represents this :
As seen in the following diagram, when the Client wants to open Google.com, it will send the request to our device instead of sending it to the Wi-Fi router.
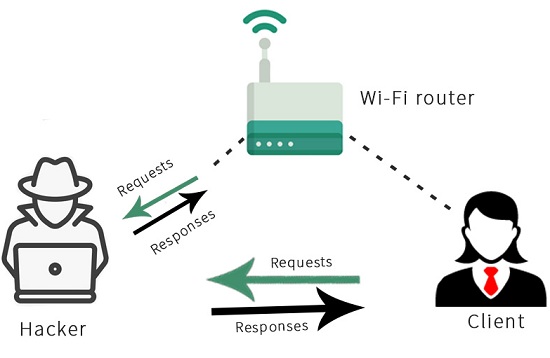
Presently, the Wi-Fi switch will send the reaction Google.com to our gadget rather than the Client, and afterward we will send that reaction to the Client. Thus, this implies that every parcel that is shipped off the Client or from the Client should go through us. Since it is going through us and we have the key, we can peruse these bundles, we can adjust them, or we can simply drop them.
Thus, that is the fundamental standard of the ARP harming or MITM assault. Essentially, we will let the Client know that we are the switch, and afterward we will tell the Wi-Fi switch that we are the Clients. This will place us in the bundle stream, between the Client and the Wi-Fi switch. After this every one of the parcels will begin coursing through our gadget, so we can peruse the bundles, change them, or drop them.






0 Comments